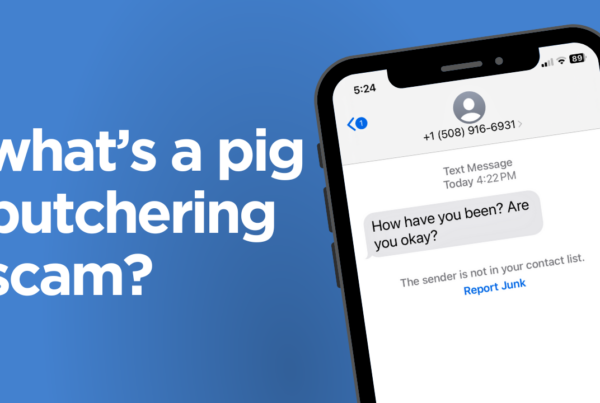
A new Canadian Centre for Cyber Security alert advises that starting in late May, a well-known ransomware group called Clop compromised a widely used managed file transfer (MFT) platform called MOVEit Transfer, reportedly impacting hundreds of companies globally.
In Nova Scotia, 100,000 current and former employees of Nova Scotia Health, the IWK Health Centre, and the public service have had their payroll information stolen — including their social insurance numbers, addresses, and banking information.
MFT platforms are used to transfer files between parties securely. Clop reportedly compromised MOVEit Transfer using a previously unknown (zero-day) vulnerability that allowed attackers to steal files from MOVEit’s underlying database.
Clop has previously targeted MFT platforms such as Accellion and has shown that it is prepared to follow through on threatened next steps. In this case, Clop threatens to identify victim companies on the Clop site as soon as June 14 and then publish victims’ stolen data if a ransom is not paid. In prior attacks, Clop has also reportedly contacted victim companies directly with ransom demands, sometimes weeks or more after the attack. Victims are not recommended to contact threat actors like Clop directly but instead work with cyber security experts to do so safely, if necessary.
MOVEit vendor Progress Software published a security advisory on May 31 about a critical vulnerability that “could lead to escalated privileges and potential unauthorized access to the environment.” It urged users to turn off internet traffic to their MOVEit Transfer environments and to install the security update immediately.
What Should Organizations Affected by MOVEit Vulnerability Do?
Organizations that may be victims of this attack should consider the following steps:
- Organizations that used the MOVEit Transfer platform with its web interface exposed to the internet should consider initiating a privileged investigation to determine if this attack impacted them.
- Organizations with vulnerable MOVEit Transfer systems should consider reviewing available guidance and patching information from Progress Software, the maker of MOVEit Transfer, and be vigilant for additional attempts at exploitation and data theft, as well as other attacks targeting these systems (e.g., the deployment of ransomware encryptors). Progress Software, the maker of MOVEit, has provided information about the vulnerability, patching and recommended mitigation here.
- If your organization was impacted, assess the attacker’s level of access and what data was compromised.
- Based on the data compromised, determine your organization’s notification requirements under applicable laws, regulations, and contracts.
- Organizations should also consider reviewing their supply chains and counterparties to determine if their data may have been exposed through third-parties use of the MOVEit Transfer platform.
Expert Advice from The Magnes Group
At the Magnes Group, we do things differently. We deliver the best-personalized insurance coverage and risk management advice with effort and care. We serve businesses and individuals who appreciate quality, precision, and value in a way that many other insurance brokerages can’t or won’t.
As an independent insurance broker, we pride ourselves on providing straightforward, uncomplicated, and honest advice. We treat others as we would like to be treated ourselves. Not to increase market share but because it’s the right thing to do. You can rely on expert advice from the Magnes Group.
"*" indicates required fields